
Through Access_Ctrl, we have enhanced personal safety and reduced unplanned downtime
strengthened Personal Safety
Only authorized and trained personnel have access to the radio control, minimizing the risk of accidents.
Preventive Maintenance
A comprehensive overview of usage data enables scheduled maintenance, reducing the risk of sudden malfunctions and costly repairs.
Lower Costs
Safer operations lead to fewer incidents, reduced repair expenses, and increased productivity.
Reduced Downtime
Early detection of wear and potential faults prevents unplanned interruptions and keeps production running.
Access Control for a Safe and Efficient Industrial Environment
In industrial settings where heavy lifting and critical processes are part of everyday operations, personal and operational safety is paramount.
Mishandling a crane can have serious consequences for both people and production. With Access_Ctrl access control, you gain complete oversight of your radio control systems—ensuring that only trained personnel with the right expertise can activate the radio control and operate the crane.
The result? A safer, more secure, and more efficient work environment.
Prevent Risks – Enhance Workplace Safety
Industrial environments come with constant safety challenges, where the human factor often plays a decisive role. By controlling access to radio-controlled cranes, only authorized operators can use the equipment. This not only reduces the risk of improper handling but also contributes to a more structured and secure workplace—preventing accidents, minimizing equipment damage, and creating a safer environment for everyone.
How does Access_Ctrl work?
Access_Ctrl is a system for managing access to radio control systems in the industrial sector. Access rights are directly linked to the radio control through RFID technology, ensuring that only individuals with the proper authorization can activate and operate the crane. Each operator is identified by a personal RFID tag or card, making it impossible for unauthorized users to access the system. Without proper authorization, the radio control simply cannot be activated, eliminating the risk of improper or unauthorized use.
-
RFID-Based Access Control
Only authorized personnel can activate the radio control and operate the crane. Without the proper authorization, the radio control remains inactive and the crane cannot be used.
-
Use Existing Cards
The system works with any RFID tag (Mifare), allowing you to utilize existing cards already in use – such as ID06.
-
Easy Administration
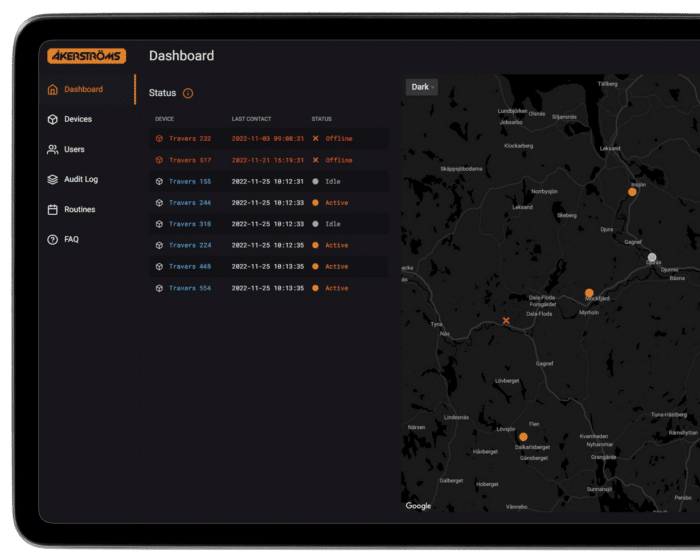
Administrators manage access rights via a web interface and can instantly see which operators are active, who has operated the crane, and when.
-
Complete Logging
All events are logged, including invalid login attempts.

Digitized Daily Inspections
Daily inspections are one of the most fundamental prerequisites for safe operations. By ensuring that the crane is inspected every day, potential issues can be detected before they lead to accidents or downtime.
With Access_Ctrl, daily inspections become an integral part of the workflow. The system reminds the operator to perform the check directly via the radio control, and all data is automatically saved—completely eliminating manual paperwork.
Scheduled Maintenance and Safer Operations
Access_Ctrl generates a production log that provides valuable insights into the condition of your cranes. By analyzing data on usage frequency and operating time, you gain a clear overview of each crane’s activity and status. This enables maintenance to be scheduled based on actual usage, reducing the risk of sudden malfunctions and downtime.
By identifying usage patterns, you can optimize maintenance efforts and avoid unnecessary interruptions. All operating data is stored locally on an LCU (Log & Connectivity Unit) and regularly synchronized with the cloud or your own server. In the event of minor incidents, production can continue without critical data being lost—you always have complete access to historical data to quickly analyze events afterward.

Talk to an expert!
Would you like to learn more about Access_Ctrl and what it can do for your company? Call or email our expert Ola or Andreas.

Andreas Johansson
Account Executive Manager
andreas.johansson@akerstroms.se
+46 241-250 55 / 070-335 61 55

